What are passkeys?
In simple terms, a passkey is a passwordless login technique that uses a cryptographic key to replace a password. It is widely regarded as the next logical evolution of identity verification over the internet. As passwords continue to lose reliability, having a secure means whereby you can prove your identity that is hardware-backed, uses industry-standard public key cryptography, and is compatible with ubiquitous devices that users already own is immensely valuable.
Why are passkeys better than passwords?
A password is only as strong as the rules used to enforce it. Tighter password policies have turned password creation into a frustrating exercise, increasing friction and reducing user experience. It introduces friction and takes away from the user experience. The strongest passwords are random combinations of letters, numbers, special characters, and symbols, but humans struggle to remember them. Even password managers are merely a stop-gap solution, as they still rely on passwords that can be phished or intercepted.
Passkeys are immune to most common password-based attacks. They can’t be guessed, social-engineered, or phished, and they use protocol-level defenses to stay secure. Brute-forcing a cryptographic key is mathematically impractical with today’s computing power. Even if an attacker captures traffic, the data is useless because the generated access codes are unique and valid only for that session.
Passkeys also reduce user friction. No more creating, remembering, or storing long passwords, a well-designed system simply prompts users to select a saved passkey and perform a quick verification (usually biometric authentication), then logs them in instantly.
Technical Background
Public Key Cryptography , the foundation of passkeys, has existed for decades. What makes passkeys viable today is the rise of personal devices, smartphones, laptops, security keys, that can generate and store cryptographic keys securely.
When you add a passkey for a site, the following keys are generated.
- Public Key: Stored by the website or app’s server. It can’t be used to access your account and is safe to share.
- Private Key: Stored securely on your personal device, never transmitted to the server, and not normally visible even to the user.
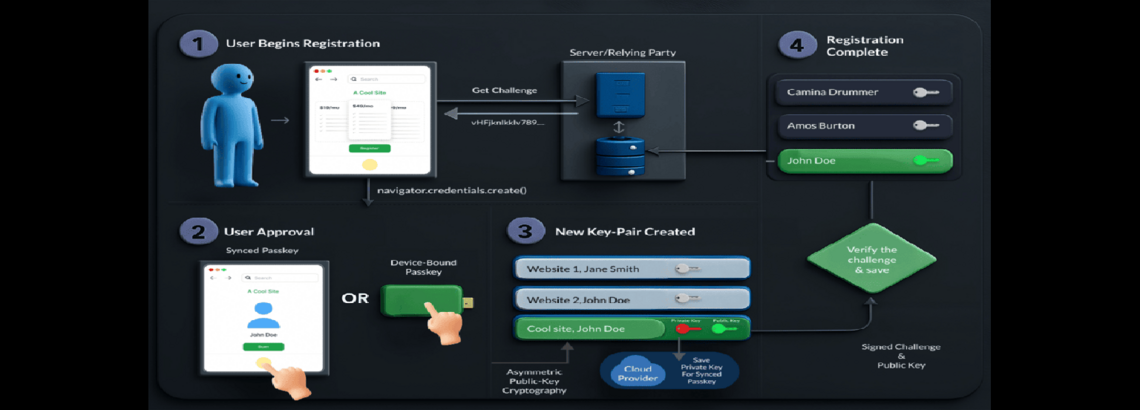
How passkeys work
Creation
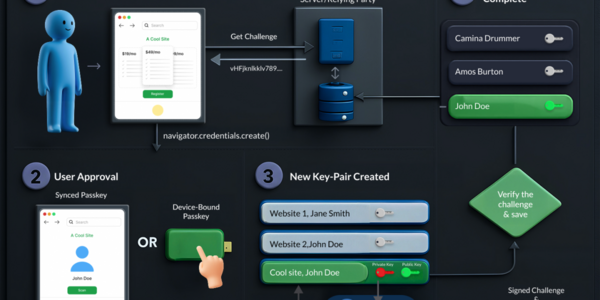
When you create an account with a passkey (or add one to an existing account), your device creates a public-private key pair. The public key is then handed over to the server against which the key is being created. The private key is stored by the user’s device, and bound to the domain name where it has been created. The storage medium could range from an encrypted web-based store, hardware-backed local device store, or even dedicated plug-and-play hardware. The last stated option is overkill for most users, but it is available and provides the highest level of compromise-proof security. The key creation process will also include a verification to make sure the generated key works properly.
Verification
When a website or app requests a verification with passkey, it sends over a unique and random “challenge” string and invokes passkey verification. The user is then prompted to select an available passkey for the domain. Users may be required to prove liveness and intent by using one of the authentication methods available on the local device (biometrics, pin etc…). The saved private key will then be used to sign the challenge, which can then be verified by using the public key, which was made available to the server during creation.A successful signing proves possession of the private key, and thereby your identity. It’s worth noting that the private key of the user never actually gets transmitted over the open internet, even over SSL. Also, each challenge is unique, single use and short lived, so even if an attacker gets access to a signed challenge, it is useless for replay attacks.
Support and Adoption
Major browsers and device vendors are already adding support for passkeys on their platforms.
Most modern personal computing devices come with some form of passkey support. Website/app owners are quickly adding support for passkeys as first and second factor authentication methods.
Major players like Amazon, Apple, Google, and Microsoft have already integrated support for the technology across their ecosystems, and the industry is quickly keeping pace.
Devices and Operating Systems
- Apple: iPhone and iPad users running iOS 16 or later can use passkeys. Mac users with macOS Ventura 13 and newer versions are also supported.
- Android: Android devices running Android 9 (Pie) or higher, support passkeys, with Google Password Manager handling cross-device synchronization.
- Windows: Windows 10 and 11 users can use passkeys, through Windows Hello. Cross device synchronization is not yet supported at the time of writing this article.
Browser Compatibility
Several popular browsers have integrated passkey support, including:
- Google Chrome (version 109 or later)
- Apple Safari (version 16 or later)
- Microsoft Edge (version 109 or later)
- Mozilla Firefox (currently with limited support)
Password Managers
Most popular password managers provide support for passkeys. They have their own implementations and mostly store the keys in encrypted web vaults along with all the normal passwords.
Perks
By using password managers, you get cross-platform support out of the box, and all your credentials live in one place. They may also offer additional features not available on your native platform, such as support for additional protocols, or other enhanced functionalities.
Concerns
You may miss out on any hardware-backed security or enrichment features provided by your native platform. There may also be some implementation differences that may cause issues on some platforms.
Examples
Notable websites supporting passkeys
- E-commerce: Amazon, Walmart, Best Buy, Target, Shopify, Kayak
- Social media: X (formerly Twitter), LinkedIn, TikTok
- Financial Services: Coinbase, Robinhood, Stripe, PayPal, Affirm
- Software Development Platforms: GitHub, Bitbucket
Need for passkey support
The internet moved away from simple sites with static pages to algorithmic, identity-driven custom user experiences decades ago. While identity security is a well-developed area of internet technology with firmly established standards and practices, the trade-off for stronger account security was often burdening users with complicated password policies and frequent Multi-Factor Authentication. With passkeys, this is no longer true. Passkeys and WebAuthn lighten the user’s load and boost account security by several magnitudes.
Even when they are not the only login method, having the option of passkeys improves overall security posture because multiple user and device protection features are built in. Users can rely on the elevated security offered by industry-standard cryptographic technology. Companies deal with fewer account compromises, reduced user churn, and less threat infiltration.
A frictionless login experience can also be the difference between gaining loyal users who keep coming back despite competition, and frustrated users who switch away for a platform with better usability.
At PIT Solutions, we have assisted clients in implementing passkey support on their platforms and noticed lower user abandonment rates and more frequent recurring logins as more users opted in to using passkeys. Users also spent less time navigating login and account steps, freeing them to access and enjoy the actual app faster.